An excellent post about Zero Trust concept from Alex Weinert from Microsoft
Original Post: https://techcommunity.microsoft.com/t5/azure-active-directory-identity/zero-hype/ba-p/1061413
In a Nutshell
Zero Trust, conceptually, asserts that traditional security models based on “the walled garden” are outdated, and that security models should assume that all requests should be treated as though they originate from an uncontrolled (external or compromised) network. Whether you think of this as “assuming breach” and operating as though the enemy is inside your perimeter or you think of this as operating in a perimeter-less environment, it’s all about operating as though you are in a pervasive threat environment. This is a simple concept, we don’t need to complicate it or dress it up because it has powerful implications.
The Zero Trust Mindset
I believe the most useful thing about Zero Trust is the mindset it creates. The mindset to adopt is that you are operating in a pervasive threat environment. An environment that demands that you continuously assess and re-assess the viability of your security strategy. Here are some key behaviors you might exhibit if you accept that you are operating in a pervasive threat environment:
- Don’t accept complacency. This is the single biggest shift of Zero Trust. In the world of flat networks and VPN, we assume that if the request is originating from a known network, it must be safe. We assume the models that protected us yesterday will protect us tomorrow. Zero Trust demands we abandon those assumptions and instead validate and exercise controls over as many aspects of access as possible, explicitly validating what we can, and accepting that the things we don’t explicitly validate remain uncertain.
- Assume all resources are on the open internet. One approach many customers have found valuable in countering their entrenched assumptions is to assume every user, device, and resource is on the public internet. Many of our most successful customers in this regard have simply moved as many resources as possible to the cloud, modernizing their security strategy as they go.
- Trust no single source. In a pervasive threat environment, accurate insights are key. A CISO once shared that “Pops told me, honest people all tell the same story, but liars lie differently.” Security models which rely on multiple sources of validation are much stronger – triangulation provides a much more accurate fix than single source validation. Similarly, control which relies on multiple elements (using device trust, location, and strong auth, for example) is better than that which relies on only one aspect of access.
- Breach containment. If we assume pervasive threats, we assume that some threats will break through our defenses. Containment strategies such as privileged identity management, role-based access, separation of duties and network segmentation can help contain adversaries who break through your first layers of defense.
- Standards are security. While innovation is wonderful, a maxim of security (especially encryption) is that nothing is provably secure, but time without breach is a good indicator. Avoid security theater or security through obscurity – heavily inspected, heavily used, and yes - heavily attacked standards provide a great anchor for your security strategy. Leverage modern authentication standards like OAUTH2, provisioning standards like SCIM, and credential standards like FIDO2 wherever possible (or buy products that do).
- There aren’t enough humans. You must automate everything you possibly can. There simply aren’t enough humans to handle the volume of telemetry and attacks you will be facing. Make use of cloud intelligence, machine learning, and most importantly automated response mechanisms like automatically locking at risk accounts or banning traffic from known bad IP addresses.
We can distill all this down to three key principles:
- Move from assumption to explicit verification.
- Adopt a policy-based, least privileged access model.
- Design with the assumption that every element of your system can be breached.
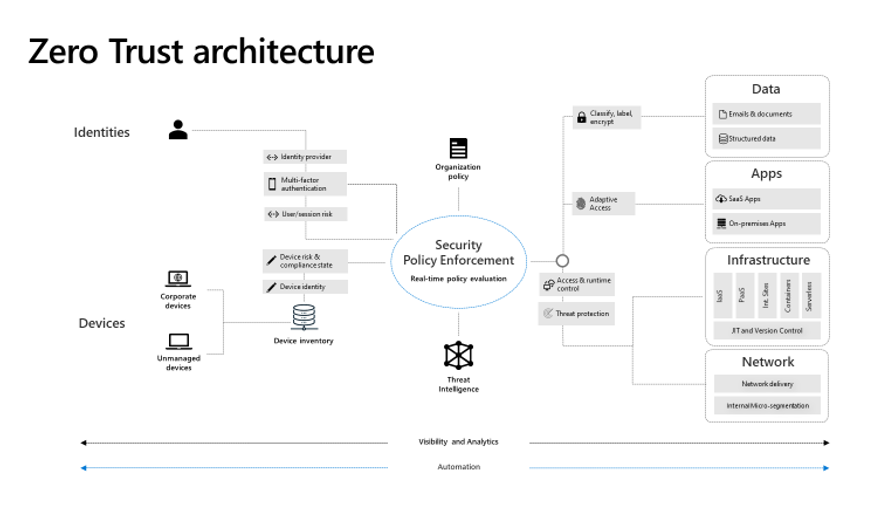
Conceptual Architecture
We have seen that successful adoption of a Zero Trust approach benefits from some critical elements. We pulled this together conceptually in a conceptual architecture, pictured below.
The critical elements are as follows. First, the key resources:
- Verify Identity. Knowing who is requesting access is essential, and that identity must be validated explicitly, not inferred from the environment. Ensure you are secure at the point of access by bringing users into a common identity system, using strong auth and threat intelligence to validate authentication.
- Verify Devices. All data access requests result in the transfer of that data to a browser or app on a device. Knowing the state of that device is critical in a world where devices can be infected, lost, or stolen. Mobile Device Management (MDM) and Mobile Application Management are critical to protecting data once it is accessed.
- Protect Data. Wherever possible, data should be protected from unauthorized transfer by auto-classification and encryption. This protects against intentional or accidental misrouting of downloaded data.
- Harden Applications. Application access and configuration must be secure to mitigate intrinsic application risks, and to ensure access is governed by policy. Application behavior, including shadow IT, should be understood and monitored for and protecting from anomalies.
- Protect Infrastructure. Where you are using cloud workloads (IaaS or PaaS), ensure you are utilizing your cloud fabric according to best security principles, utilizing the intelligence and protection provided.
- Govern Networks. Mitigate lateral movement by using an intelligent, adaptive segmentation strategy for workloads, monitoring for and protecting from anomalous traffic patterns.
Then, the key tools to tie it together:
- Policy driven access. Modern micro-segmentation means more than networks. It requires we also gate access based on their role, location, behavior patterns, data sensitivity, client application, and device security. Ensure all policy is automatically enforced at the time of access and continuously throughout the session where possible.
- Automated threat detection and response. Telemetry from the systems above must be processed and acted on automatically. Attacks happen at cloud speed – your defense systems must act at cloud speed as well, and humans just can’t react quickly enough. Integrate intelligence with policy-based response for real-time protection.
Next Steps
Here are some next steps and related on demand sessions to help you go deeper on how to get started today:
Identity Teams:
- Connect all your apps for single sign-on – Identity is your control plane, but only for apps and users that are visible to it!
- Ensure strong identity with multi-factor authentication and risk detection.
- Enforce policy-based access and least privileged access for breach containment.
- Check out these sessions:
Device Management Teams:
- Register your devices with your Identity provider so you can consider device context in your policies.
- Implement MDM security baselines with compliance reporting.
- Implement role-based access control that allows view access for impact assessment.
- Check out this session:
- DEP50: Why Microsoft 365 device management is essential to your Zero Trust strategy
Network and Infrastructure Teams:
- Enable a cloud workload protection solution across your hybrid and multi-cloud estate.
- Use cloud-native controls to create micro perimeters.
- Reduce attack surface by implementing just-in-time application and network segmentation.
- Check out these sessions:
Application and Data Teams:
- Perform shadow IT discovery and implement a cloud control program – you can’t manage what you can’t see.
- Agree on a label taxonomy and classify documents and emails – use default taxonomy for initial classifications.
- Apply protections to high risk scenarios such as sensitive data and unmanaged access in apps.
- Check out these sessions:
Finally, check out our Zero-Trust center and especially the maturity model which we hope will help you think about next steps on your journey.